Forensic Report Raises Questions about Australian Tax Office’s Handling of Craig Wright Probe
Introduction
We recently took the time to lay out a factual timeline of Craig Wright’s involvement with Bitcoin using publicly available information. While the list is not exhaustive, the bulk of information comes starting in 2014 as everything prior to that date has been scrubbed from the internet. When digging in to try and fill in the gaps between 2009–2013, you find a long and bitter battle between Wright and the Australian Tax Office. The BBC first asked Wright about his dealings with the ATO in his famous interview around May 2016. Here is his response:
I have companies that are under audit. The reason for that is that we have told the ATO everything. We have told them about the tax issues and implications. We actually put in everything with the auditors… We had an internal audit and we supplied that to the tax office so that we could pay the correct amount of tax. And because no one really understands Bitcoin very well, and no one understands the timing or anything like that, then it’s still an ongoing matter.
While many news organizations have used Wright’s dealings with the ATO to make accusations of “fraud”, an examination of the facts and evidence paints a different story. We have obtained private documents that contradict the prevailing narratives about Wright’s history and dealings with the Australian Tax Office:
- Wright‘s saga with the ATO dates back as early as the 2009 tax season.
- Wright was working with the Australian Tax Office to properly report tax on his Bitcoin businesses.
- Questions are raised about the Australian Tax Office’s handling of the various audits against Wright’s companies — specifically forensic analysis suggests fraudulent documents were used as evidence against Wright and a large security vulnerability existed in the ATO’s networks allowing modification and altering of records.
Background
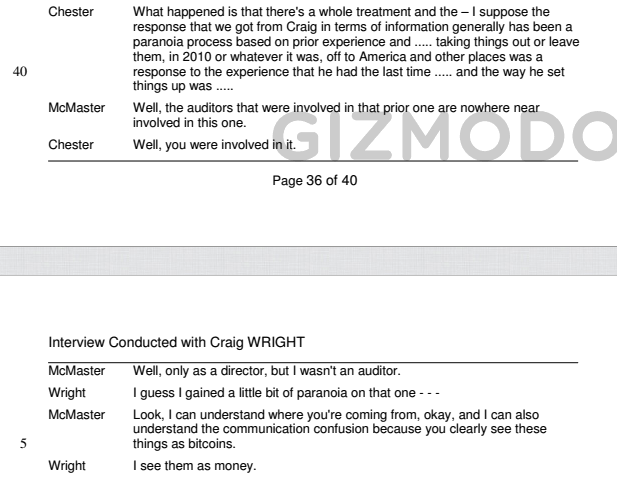
As part of Wired/Gizmodo’s initial doxxing of Craig Wright, a leaked 2014 transcript between the Australian Tax Office and Craig Wright and his legal team gave us a glimpse into the long saga between Craig Wright’s various business dealings and the ATO. This document is authentic and is cited as evidence in the current lawsuit between Ira Kleiman and Craig Wright. In this transcript we are given some key insight into the various audits Craig Wright’s companies underwent as a result of his Bitcoin businesses dating back to 2009. Two days prior to the date of the transcript, Investor Daily reported that Wright was working with the ATO to “have a full banking licence from APRA based on Bitcoin” with his company Hotwire PE. The transcript shows that this was not Wright’s first experience with the Australian Tax Office surrounding his Bitcoin businesses, and specifically that he “gained a little bit of paranoia” from his prior experience with the ATO “in 2010 or whatever it was”:
In working to obtain information about this previous interaction, we have obtained exclusive documents showing Wright’s initial 2011 objection decision against an amended assessment for the tax year ending 30 June 2009. The audit for the 2008–2009 income tax year was commenced on 10 February 2010.


The document details that Wright “purportedly sold [his] personal intellectual property to Information Defense and Integyrs”, two of Wright’s companies.
Information Defense was created on 29 January 2009, 19 days after the mining of the first Bitcoin block, and the domain information-defense.com was registered on 23 January 2009. The domain for Integyrs.com was registered on 25 April 2009.
It’s noteworthy that Wright’s initial tax return claimed a net capital gains upon which he would have owed taxes — refuting many claims that Wright was trying to get money out of the Australian Tax Office. After audit, the ATO took up issues with Wright’s claimed deductions to which he filed an objection. While the objection was initially disallowed, the objection decision was later reversed (as shown in another document dated 11 February 2013) and the deductions were finally granted to Wright. It is noted that “the Tribunal is requested to note that this decision is in favour of the Applicant”:


The 2 year delay in approving Wright’s initial tax return for the 2009 tax season outlines the troubles Wright had in running his companies while under audits that he viewed as invasive and unfair. In the 2014 meeting he presciently tells the auditors “I did my best to try and hide the fact that I’ve been running bitcoin since 2009 but… by the end of this I think half the world is going to bloody know.”

During the middle of this audit in an alleged email between Craig Wright and Dave Kleiman dated 22 May 2012, Wright expresses frustration with the ATO’s “BS’ing” where he guesses “that they want to get a result out of attrition rather than honesty” and that “they will drain all I have if they can”. Wright continues venting his frustrations saying “They lost evidence and use my temper against me. I hate their lies. I did everything right and I am STILL punished.”
Craig’s aforementioned paranoia is on display in the early parts of the February 2014 meeting when Wright identifies that a private ruling issued by the ATO on 30 September 2013 was actually issued on 29 November 2013 and backdated. The backdating of the ruling was only discovered once Wright went to Internal Fraud and Investigations and had the authorization number investigated. Des McMaster, one of the auditors, shows frustration that Wright had obtained this information:

To add on to the dispute, Wright and his attorneys asserted that they had not received notice of the ruling

Questionable Evidence
Two months after this February 2014 meeting with the ATO, on 15 April 2014 the ATO reached out to Ira Kleiman and provided Ira with copies of purported agreements between Wright and Dave Kleiman. Ira begins to distrust Wright from this point on, and it is two weeks later where Wright, in a message to Ira, accuses the ATO of fabricating documents:
In this, I have a GST debt, the company has a gain. On the software from WK to Coin-Exch, I have an overall GST debt owed of $3.7 million (give or take). The company gets a return of 3.7 million. The net outcome is zero tax as they cancel.
What the tax office can do is use this and hold payments back to the company. They are trying to fish. They want information that they are not legally entitled to have. So far, they have fabricated documents (and been caught), used half-truths to make it seem as if things are wrong to others and more.
We have exclusively obtained two Computer Forensics Reports performed on behalf of Wright’s company Demorgan Ltd where computer forensics expert Dr. Nick Sharples and digital forensics expert Alan Batey were independently appointed to examine email messages used in the ATO’s probe of Wright. These emails were used as evidence in the continuing audits and probes of Wright’s business dealings that culminated in the ATO raid on his Australian residence in December 2015, one day after Wired published an article accusing him of being one of the people behind the Satoshi Nakamoto team.
Sharples Report
Dr. Sharples performed his forensic analysis on November 2015:

Of the four emails examined by Sharples, there is one email in particular that we will focus on for the purpose of this piece. This email, named DM5 in the forensic report, is given the title “ Private Ruling application Hotwire Preemptive Intelligence Pty Ltd DLM FOROFFICIAL-USE-ONLY .msg” and dated 01 November 2013. The title suggests the email is related to the notice of the private ruling supposedly issued on 30 September 2013 that Wright alleged was actually issued on 29 November 2013 and backdated. In the original 2014 transcript, Wright’s lawyers argue this ruling was never received:

Sharples notes immediately that there are two different Content-Type fields contained in the headers with different values. He notes that he does not know “how such a message could have been constructed.”

To understand the forensic report, we must become familiar with two pieces of email authentication. Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) are email authentication methods designed to detect forged sender addresses in emails (email spoofing). SPF allows the receiver to check that an email claiming to come from a specific domain comes from an IP address authorized by that domain’s administrators. DKIM allows the receiver to check that an email claimed to have come from a specific domain was indeed authorized by the owner of that domain.
Sharples notes that there is no SPF check or DKIM signature for this email:

In his conclusion, Sharples reiterates that the first (of two) Content-Type header fields contains an encoded date that is not consistent with the date the email was sent. This implies the email was not sent at the same time it was constructed.

Finally, Sharples concludes that the “inconsistencies with the email header values… raise questions in my mind concerning the provenance of the message.”

Similar analysis is performed on the other three emails in the report, and similar inconsistencies are found. Sharples notes specifically that “the ato.gov.au email system is configured to include the email header field ‘content-transfer-encoding’, and that none of the emails… have that field present, despite having purportedly originated from that domain.”
Batey Report
Dated 11 November 2015, Alan Batey also performed an independent analysis on a set of emails. He also performed analysis on email DM5.


Batey confirms that there is “neither an SPF or DKIM record present” for DM5, yet passes the SPF test “possibly due to their parent SPF record” (meaning it passed the SPF test for sge.net). Further analysis of “information available in the header of DM5 shows that the email was delayed for 2 days while in transit… [and] given the delay and the lack of signing of the email there is no assurance that the email has not been altered at the final hop.”

With all of this said, Batey comes to an even further startling conclusion: “The SPF record of DM5 shows that an additional 544 host are able to send on behalf of ATO.GOV.AU” and specifically that “any address from sge.net is permitted to send on behalf of ATO.GOV.AU”.

Batey’s analysis shows a potentially massive security hole once existent in the ATO and raises serious questions about the authenticity of the email used as evidence against Wright. Batey notes that “the email DM5 originates from sge.net and its SPF record contains an IP range’s of over 130,000 IP addresses… whereas the ATO address is limited to 4 IP addresses… This large IP range could be considered a potential security flaw as it allows emails to be sent from any one of these IP addresses and still pass the SPF test.” You can read Batey’s conclusion here:

Conclusion
Authenticity of Documents are Called Into Question
The independent analysis done by Sharples and Batey indicates that there was a potential security vulnerability in the ATO’s networks while handling Wright’s case and specifically that there are legitimate questions regarding the provenance of individual emails used as evidence in the Wright case. It is noteworthy that Wright commissioned the independent forensic analysis just one month prior to the leaking of information about Wright’s supposed identity as Satoshi Nakamoto to Wired. As Ian Grigg has implied coordination between Wired and the ATO during these events, the timeline in light of this new information does raise questions themselves.
Looking at the analysis of email DM5 and the surrounding timeline of events, there are three insights that emerge:
- It appears that the ATO backdated a private ruling to Wright’s company Hotwire PE, a clear violation of law.
- There are many questions raised about the authenticity of many emails used as evidence against Wright, but specifically in regards to one email that appears to be related to a notice of the private ruling that Wright’s attorneys never received notice of.
- Independent forensic analysis showed a large security vulnerability in the Australian Tax Office’s networks that allowed for records to be altered and forwarded without being recorded.
With all of this said, it also raises questions about the authenticity of documents provided to Ira Kleiman by the ATO. These documents are being used as evidence in Kleiman’s lawsuit against Wright — some of which Wright has denied the authenticity of.
